DFOH is a system that aims to detect forged-origin hijacks on the whole Internet.
Forged-origin hijacks are a type of BGP hijack where the attacker manipulates the AS path
of BGP messages to make them appear as legitimate routing updates.
DFOH is useful given that the BGP extensions proposed to cryptographically
verify the validity of the AS paths (such as BGPSec or ASPA) are hard to widely deploy.
With DFOH, operators can quickly and with high confidence know when their IP prefixes are being hijacked.
How DFOH works
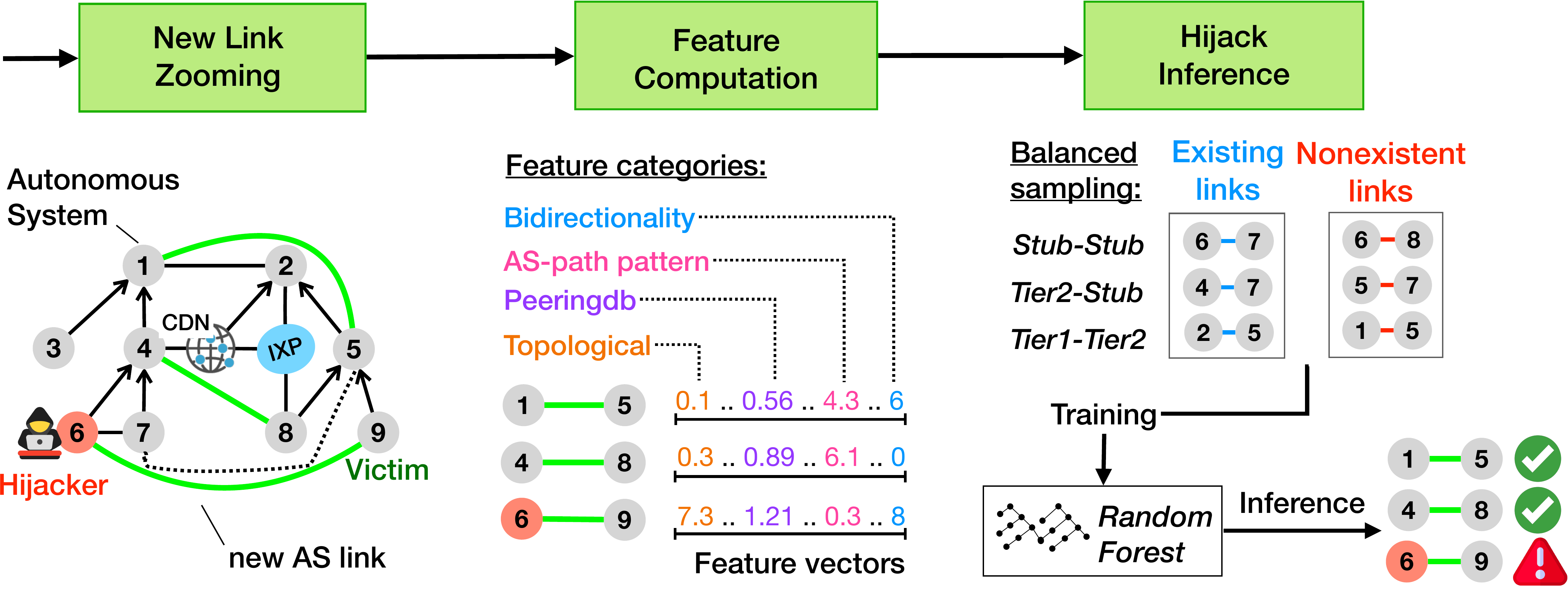
DFOH detects forged-origin hijacks using a three-steps approach depicted in the figure below.
- DFOH finds new AS links by parsing the AS paths of BGP routes collected from RIPE RIS and RouteViews.
DFOH zooms on these new AS links because a forged-origin hijack likely triggers the appearance
of a new AS link between the victim and attacker (in case of a Type-1 hijack).
Yet, most of the new AS links are induced by legitimate events such as new peering agreements. Thus, the following steps aim to discrimante the fake AS links from the legitimate ones. - DFOH computes a set of features for every new AS links detected. The features can be divided into four categories: topological, AS-path pattern, peering and bidirectionality. We carefully chose this set of features to make DFOH accurate upon various attack scenarios and robust against adversarial inputs.
- DFOH uses an inference pipeline that is similar to what state-of-the-art link prediction frameworks use. However, the training part of the pipeline relies on a balanced sampling algorithm that makes DFOH robust against routing biases and prevents DFOH to overfit for one particular attack scenario.
How DFOH performs
We evaluate DFOH on forged-origin hijacks that we artifically created and found that it discriminates the fake AS links from the legitimate ones with high accuracy: It correctly pinpoints 90.9% of the suspicious cases and only incorrectly classifies a legitimate cases as suspicious in 1.9% of the cases. Besides, DFOH remains accurate regardless of who is the attacker and the victim.
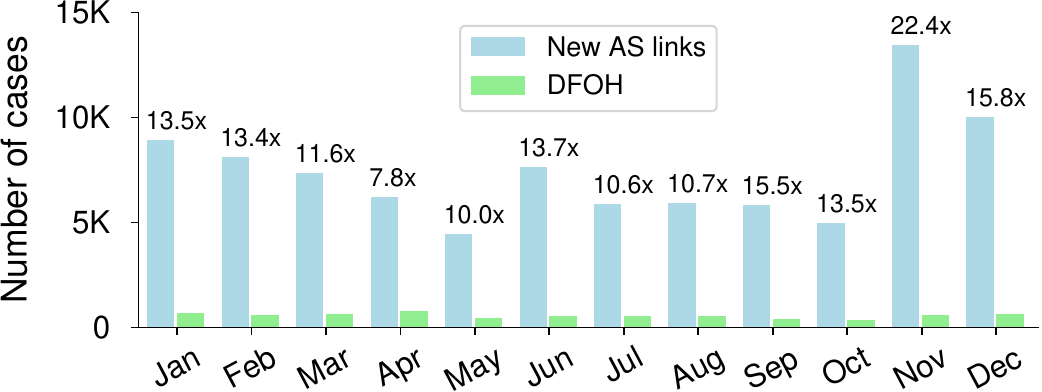
As shown in the figure on the left, DFOH greatly reduces the number of reported cases compared to simply reporting all the new AS links. Network operators can more easily find the suspicious cases that involve their AS and more quickly trigger countermeasures.
